Net Neutrality 101 – Background
Net neutrality (NN) is a topic that has been frequently bantered about and there has been much debate on the subject, much of it redundant in nature, oftentimes nebulous and obscure in its presentation. There have been countless articles written on the topic, and at all levels. When I initially investigated the debate, I was both surprised and overwhelmed at the plethora of information actually available. Part of my surprise came from the fact that the more I read, the less I seemed to actually grasp the true essence of the matter at hand. I realized that I required a basic understanding of the underlying principles before I could actually examine the question of how, or indeed even if, net neutrality relates to and affects questions of national security.
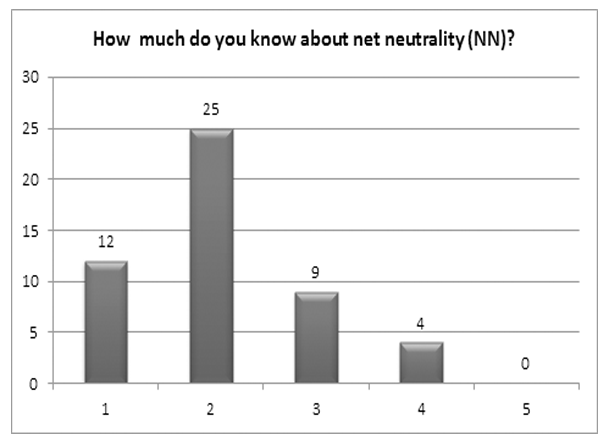
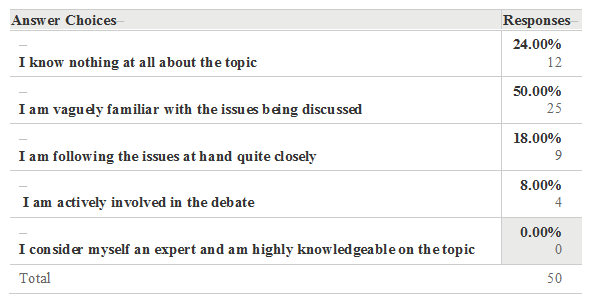
In an attempt to gain broader insight as to the depth of global understanding of both a general and a specialized public, I conducted two different surveys. The first was a 6 question survey “Net neutrality, what does mean to you,” to try and obtain a glance at people’s awareness on the issues concerning the net neutrality debate in general. Precise, multiple choice questions were posed in an attempt to rule out speculative responses. The second survey was composed of only 2 items concerning NN and how it relates to national security and there were a total of 32 respondents. In order to obtain a homogeneous balance, the surveys were conducted using populations drawn from 2 sources: both social media oriented, but the first with a more general audience (Facebook) and the second, more professionally oriented, targeting specifically intelligence and police orientated groups (LinkedIn). Below are the findings of the first survey, of which there were a total of 50 respondents. The results of the second survey will be presented in a later portion of this article.
Net Neutrality, What Does It Mean to You?
Survey Results 1
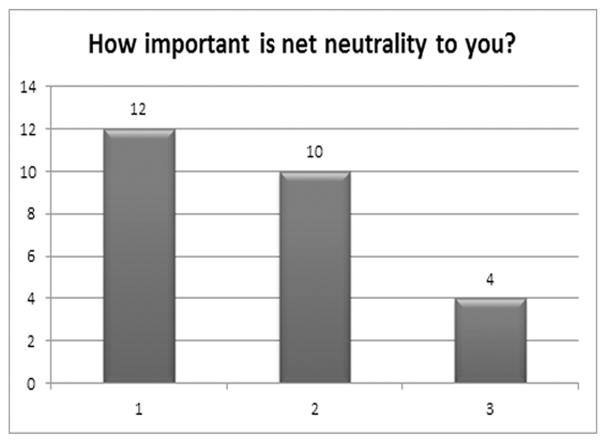
How Important Is Net Neutrality to You?
Survey Results Q2
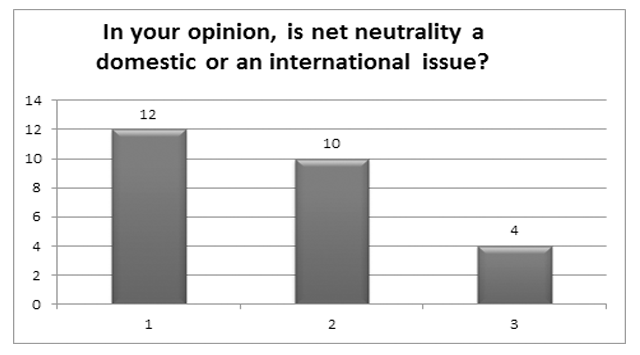
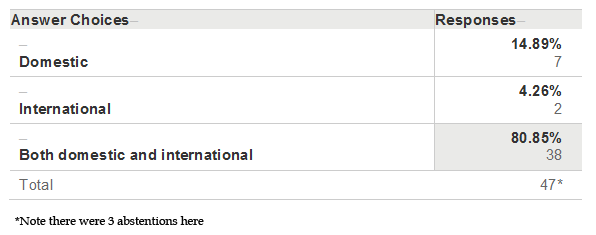
In Your Opinion, Is Net Neutrality A Domestic or An International Issue?
Survey Results Q3
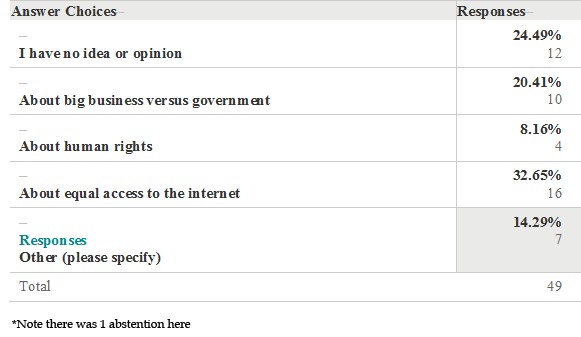
If You Have Adopted A Stance, Where Do You Place Yourself in the Debate?
Survey Results Q4
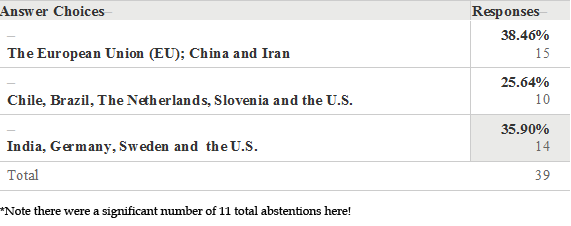
Which States Have Officially Enacted Net Neutrality Legislation in Your Opinion?
Survey Results Q5
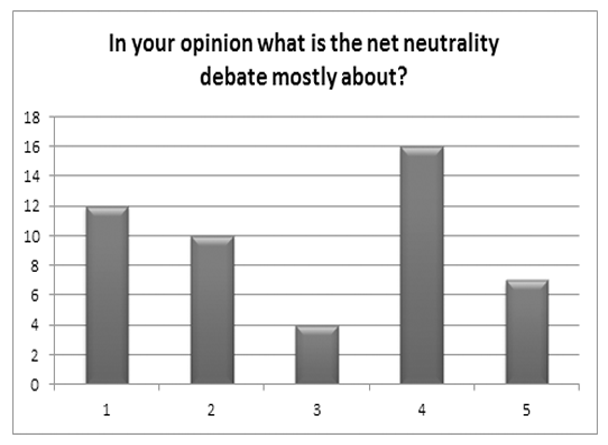
In Your Opinion What Is the Net Neutrality Debate Mostly about?
Survey Results Q6
Responses:
- Handling data by the provider: slow down or accelerate
- free market vs. governmental regulation
- freedom of speech and independence from the government to access information freely
- Control
- It is about small business vs big business having a level playing field [sic] for potential costumer [sic] access.
- Control
- It’s about government sticking its nose where it isn’t needed.
Survey Results – General Comments and Conclusions
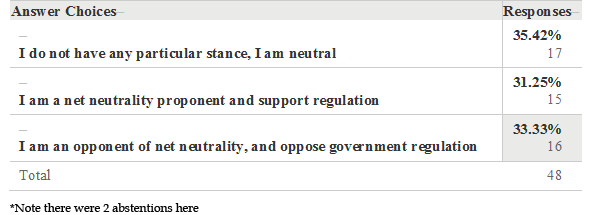
According to the results and the analysis it would appear that a large number of individuals are either unaware of the issues involved in the debate or, are otherwise unconcerned with their potential impact. While there is a segment of the populations which can be discerned to be quite knowledgeable and interested in the subject they remain nevertheless a significant minority. Best, rough estimates according to the results of this survey (correct answers and factual responses taken into account in this determination) appear to be in the range of 10 – 15% of those interviewed.
There were two significant findings: First, of 50 persons polled, not a single one considered themselves an expert on the topic, despite some being involved in either national security or IT fields. Secondly, was the lack of response to question 5: “Which states have officially enacted net neutrality legislation in your opinion?” This question had an abstention rate of 22%, and a correct response rate of only 25.64% (the lowest). This contrasted sharply with the 80.85% response level indicating that NN is both a domestic and international issue. This seems to indicate that the respondents are perhaps US-centric or lack a sense of an international relations perspective on the issues, or perhaps both. This reflects that international perspectives were somewhat limited.
Scholarly Research
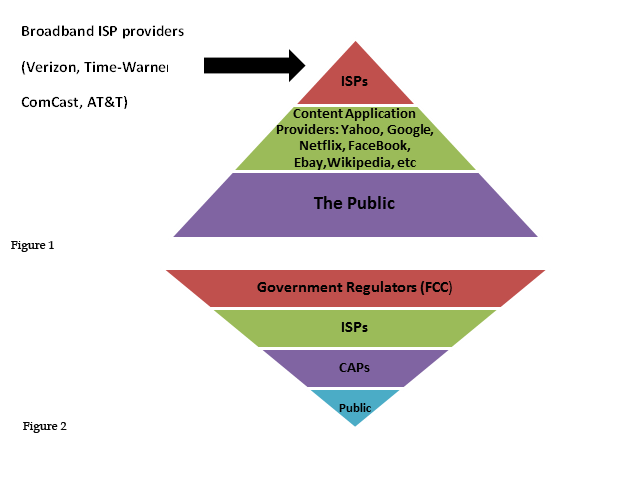
I spent the better part of several weeks examining various articles and presentations ranging from official discourse to, popular and specialized trade journals as well as peer-reviewed, academic analysis. While this issue has international and global ramifications, much of the analysis presented will be US-centric, since they have been, and are, the ones actually pulling the strings of international telecommunications industry [1]. The overall consensus I was able to draw was net neutrality is largely a tripartite struggle between several entities: First there are large vested corporate interests represented by ISP providers, who hold the lion’s share of the market, these interests stand in conflict with a heterogeneous conglomerate of assorted interests including human rights activists, large content application providers (CAPs) such as Amazon, Yahoo, and Facebook, a small group of the intellectual founders of the initial architecture framework, big government, and a large movement of assorted net neutrality end-user groups.
Much of the argument, both for and against net neutrality is paradoxically based upon the same premises, albeit adopted under different paradigms. The important issues are: regulatory practices, network management, privacy, broadband congestion and delivery speed, encouraging future innovation, free access to users and startups, and of course profit and investment. At its core the debate is largely drawn along political lines with a direct confrontation between Democrats and Republicans and big business America facing off with the executive branch, with Obama himself entering into the debate. Below is a simple schematic that points out the two alternative views of market regulation principles, including a top down approach where big business and the ISPs would determine access (Fig 1), and that of a bottom up approach representing the interests’ of government regulators in a bottom up, government regulated matrix (Fig 2).
A Domestic Issue with Global Impact
The internet is and remains a largely Western venture and the US has the largest controlling interest in the medium, since many of the largest content application providers are based in the US. Globally, there has been concern that developing countries will not be able to have a greater active role and participation in the development and spread of this new technology. In light of these concerns, it comes perhaps as no surprise that Chile, a low end user, was the first state to adopt national net neutrality legislation, back in 2010 [2]. Developing countries such as Chile adopted a system known as “zero-rating,” whereby large international CAPs, such as YouTube, Google and Facebook, offered a barebones version of their applications for little or no fees, thus allowing the public cheap and easy access. This served the purposes of interesting the public, largely through broadband, wireless, mobile telephony, and introducing the new medium. Unfortunately in the case of Chile, the net neutrality principles of “all bytes being created equal” was applied and the special zero-rating went the way of the dodo on June 1, 2014 [3].
The other states to have adopted net neutrality legislation in their national frameworks include the Netherlands, the second adopter in 2011, Brazil on April 22, 2014, and Slovenia[4]. The European Union (EU) is in the process of policy adoption, and the US just recently passed a most contentious solution to adopt net neutrality rules, and reclassify broadband usage as a public utility, under the currently existing Title II legislation [5]. The interests are large and the fight is certainly not over yet. This succinct introduction and partial analysis of what net neutrality is about, helps to offer an overview of the process and the issues at stake as they pertain to the public at large. This also clarifies the current international situation as it pertains to national legislation.
National Security
National security issues sort of got waylaid in the run up to the FCC regulation debate. The issues were lurking in the background much as good spies are meant to do. Ironically, despite the not too distant revelations concerning NSA snooping and the uproar it caused, the issue of net neutrality was never really connected to that debate, nor conversely was national security an issue raised to any significant extent during the push for gigabyte freedom. This oversight may have been intentionally and conveniently created by a chronically embarrassed administration, which has been accused of carefully orchestrating diversions in the past, when faced with scandals such as fast and furious, IRS targeting or the tragic events in Benghazi. Alternatively, there has been an increasing lack of transparency in the current administration, despite claims to the contrary. Its practice of classifying anything it does not wish to be made public, as a matter of national security, may be yet another alternative explanation as to why an association might not be readily obvious. Regardless the actual cause, the end result is an uninformed public.
Running through several well-stocked, online university libraries, much to my astonishment, I was unable to root out any significant reference materials relating to this topic. Either nobody has considered it important enough to write about, or they simply do not see the connections. There were a couple of rare exceptions, and I had to base my investigative research on those few presentations. Of course, a researcher’s objectivity is lessened proportionally by the lack of references he or she uses to do their analysis. The rest is drawn from hopefully enlightened and complementary conjecture on my part and hypothetical models I have drawn from my understanding and the limited number of available references.
Attempting to evaluate the issues surrounding the NN debate requires walking a thin line between two diametrically opposing camps of thought. The positions are so rigid and well defined that is difficult at times not to be convinced by the arguments and to topple into one side or the other of the argument. The function of a researcher is, however, to remain unbiased, neutral and to present the facts and nothing but the facts, and this is what I have attempted to achieve here. Once having completed a research, however, it becomes increasingly difficult not to adopt a position. I will present the position I adopted as a result of my inquiries in the conclusion. Thus I expect this article to be quite controversial, which is a good thing.
There are two distinct aspects of net neutrality and how they relate to national security which I will discuss. The first has to do with cyber espionage and terrorism (two related offspring) and the second has to do with censorship, which may or may not be related to questions of national security depending upon the case at hand. There is a third element related to these previous two that is worth discussing even though it only really relates peripherally to national security and that is criminal activity and solicitation.
In this article I am posing the question of whether if and how the issue of net neutrality may play out in the intelligence gathering and national security environment. If the revelations of Edward Snowden are anything to go by, then we may indeed have concerns about having the government watching over the internet henhouse as it were. As it currently stands, it is still too early in the game to make any real calls on the subject, and as has been so rightly pointed out by friends and colleagues, there are a host of other significant variables and considerations involved, not the least of which are the domestic versus international approach to the topic and the different facets which this technology and the issues involved represent, such as deep packet inspection (DPI technology) National Security Letters (NSLs).
National security may be regarded, domestically from an inward, looking outward matrix, but also looking toward the broader spectrum of international cooperation and this is yet another aspect to be taken under consideration. This world view has always been a two tiered approach; politically, bureaucratically, strategically as well as operationally. We face many of the same issues in regards to internet technology and national security as we do for other issues such as international crime (drug and human trafficking…), terrorism, piracy, copyright legislation and so forth. This is why it is important to address the issues in a format relating to international relations.
Once again, however, we are faced the seemingly eternal polemical divide between individual state sovereignty as ensconced in the principles of the Westphalia treaty of 1648 and a real need for coordination and control at the international level. These two facets are and probably will remain is a state of polar conflict for the foreseeable future, and go beyond the scope of what I hope to accomplish here, which is simply raising awareness of the situation, opening the debate, and trying to clarify the eventual correlation and relationship which exists between net neutrality and national security. How are they dissimilar?; what common goals might they have?, and how might they come into conflict?, are just a few of the important questions this relationship raises and which need to be answered more fully. Immediately, we can recognize that control by a government body over a framework of telecommunications means that the possibility for government intervention control and censorship are augmented. This is one important point and a possible danger, which has been largely overlooked in the rather Kantian Utopian euphoria of the recent net neutrality jubilation It is not a question that it does not already exist, just that it will now be easier than ever to exercise since a government entity has taken over regulation of the systems. While I am not suggesting intentional governmental malfeasance, one of the things I have learned in my career is that any system that can be potentially misused by any organization eventually will be. This is all just a part of risk analysis and threat mitigation.
Bytes v. the People
Part of the paradox I have uncovered is that those who are calling for greater human rights and respect for the freedom of individual privacy are asking the largest abuser of those individual rights and freedoms to serve as the guardian and watchdog of those very rights. Thus inadvertently, perhaps the NN advocates may be shooting themselves in the foot. Again, this remains to be seen, but is worth considering.
The principle of all bytes being equal and allowed free passage throughout the telecommunications network is hopelessly idealistic. Governmental probing, abuse of the telecommunications systems and intrusion into individual privacy have been well documented in the recent past, as pointed out by Edward Snowden [6]. Governmental reclassification and the decision to regulate the internet as a public utility, much the same way as wired telecommunications, means that the government will gain greater authority and interest as a result. Quite simply this means they have a greater vested interest and one of those interests is national security. Some will respond, quite rightfully that this is a good thing. Surely the safety and the security of its citizens are the primordial concerns of any state. The catch is that there is always a trade off when it comes to individual rights and freedoms. As the looming menace of terrorism fades, slowly into the sunset, people become more concerned with their own individual rights as opposed to those of the collective whole. The recent collective response to the outrage over the NN debate paradoxically is just one prime example of such a manifestation.
The Abuse, the Whole Abuse and Nothing but the Abuse…
There is no question of abuse, be it at the governmental, corporate or individual level, rather one of degree. Upon closer scrutiny and after several studies it becomes increasingly clear that internet traffic is and has been impeded at different levels and in different contexts, to different ends. In its most simple representation corporate abuse concerns vested economic interests, whereas those of big government revolve around power, control and questions of national security.
The Surveys
Survey Results
Survey 1
Survey Results
Survey 2
Survey Results – General Comments and Conclusions
In an attempt to obtain a broader, more inclusive cross representation of internationally aware and professionally based opinion, the second survey was more widely distributed via the professionally oriented social media site LinkedIn.
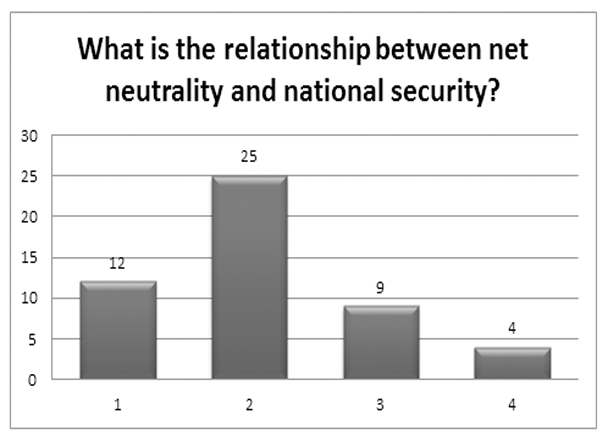
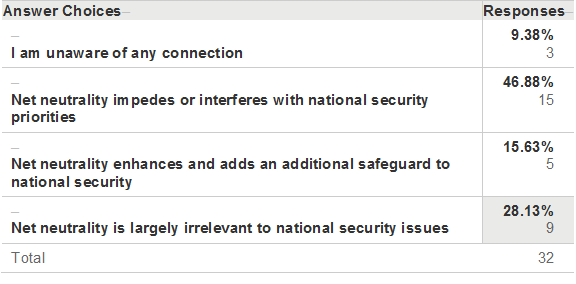
The most significant and interesting finding, which actually underscores my own personal hypothesis elicited at the outset of this research, was that enactment of net neutrality legislation actually impedes or interferes with national security priorities. It is difficult to determine the precise interpretation of this response, because I failed to request further clarification, however it does determine that at least 46.88% of respondents, the vast majority, perceived an inherent conflict between the NN protocols and questions of national security. This leave the topic open for debate and further research.
The “What If” Protocol
Much of the case behind the movement of gigabyte freedom was based upon unsubstantiated contentious issues of “what if.” What if the industry developed a 2 tier system of access? What if the industry throttled, chocked or otherwise impeded traffic, etc., etc. None of these issues were actually a reality to any major extent, rather based upon speculative musing and a few minor cases of actual infringements (largely European based). The industry had a pretty good record at self-regulation. This is not to say that the arguments were totally unfounded, rather the response to the posed or implied threat was radical in the extreme. Rushing full speed from privatization to state controlled oversight in such a short period of time, with several significant policy changes and such heated debate thrown in for good measure, indicate a lack of measured analysis and reflection on the topic and a rash and rhetorical decision making process.
Censorship, Terrorism and International Criminality
The question of national security arises in relation to international criminality and terrorism, both of which pose similar concerns in the effort to combat them. Censorship is one method governments have used to filter out information and recruiting strategies from terrorist groups, and rendering this information inaccessible to the public. This is precisely the inverse of the concept enshrined by NN. Other governments such as Iran or China have practiced censorship in order to bolster their regimes, avoid criticism and the importing of what may be deemed as questionable input. These strategies are carried out for the enforcement of political or religious reasons. Intrusive inspection techniques have assisted law enforcement and security agencies in obtaining leads and information on both terrorists and transnational crime syndicates.
The censorship is conducted through surveillance techniques. The most common technique is that known as “deep packet inspection, or DPI. DPI is carried out on three different levels: shallow, medium and deep [7]. Stalla-Boudillon, Papadaki and Chow define DPI as, “technologies [which] are able to make anything that happens on a network visible and recordable. They do, however add an important caveat that, “this is only possible when the payload is in plain text” and further point out that, “where encryption is used the ISP would then need to be able to break the encryption in order to inspect the payload.”[8] Of course, as might be imagined, government agencies, such as the National Security Agency (NSA) are capable of easily decoding and breaking down even encrypted materials.
Two major weaknesses inherent to the framework and architecture of the internet itself and which expose it to attacks from the outside are the fact that the internet was designed as an isolated end user application. This means that each individual must be responsible for their own cyber security in the long run. Secondly, Virtual Private Networks, (VPNs) were an unforeseen afterthought in the development of internet communications but pose a threat to cyber security. Another important concern, besides crime, terrorism and copyright infringement, raised in the recent European debates on NN, has been that equal access to all might well weaken the campaign against child abuse images and materials [9].
Thus the concerns are real and they are significant. Part of the Obama administration’s plans to enhance cyber security, are founded upon a more intensive effort to combat both terrorism and cyber crime using advanced security methods, inspection and protocols. It is evident that such a program would necessarily conflict directly and importantly with the concepts embodied in net neutrality, where all bytes are created ostensibly equal. In one of the very few articles dedicated to examining the issues in a clear and straight forward manner, NetCompetition pointed out several of the evident discrepancies in the Obama administration’s rhetoric concerning net neutrality and cybersecurity. It is even more astonishing that this article is so incredibly prescient when considering it was written 6 years ago. Obama referred to cyber-attacks with the rather “cutesy” and disingenuous epithet of “weapons of mass disruption. Yet the fact that the administration has made it a priority speaks volumes about the approach they intend to adopt in the future [10].
Thus, when it comes to the administration’s promises of, if you like your easy internet access you can keep it, and the presentation of the government as the protective watchdog of the people, may ring a little false to those who lost their private health care coverage and who may be hearing echoes of previous failed promises. NetCompetiton also forcefully stated that, “In effect the emphasis on cybersecurity appears to actually take off the table the extreme net neutrality position of an end-to-end architecture principle where no byte can be interfered with in any way.”[11]
This position of exposing the obvious paradox of dichotomous US government policy in general and that of the executive office in particular, seems especially strong and well-founded when compared to other, more opinion-based, articles in support of NN. One such example is a piece written by Spandan Chakrabati, whose argument is that net neutrality is actually an essential complement to national security. Chakrabati writes that, “The greatest guarantor of the security of a free state is not a well regulated [sic] militia, but an informed citizenry that does not live under censorship from its government or its corporations (Chakrabati, 2006).”
Despite Chakrabati’s poor understanding of constitutional law in regards to a well-regulated militia aside, the author seems to have ignored the inherent relationship between intrusion and censorship. Finally the author totally discredits his stance when he asserts, “It fits the conservative mindset to control the free flow of information (you know, the people can’t be trusted with all this info), and it fits the liberal mindset to preserve that same flow (Chakrabati, 2006.” It becomes immediately evident which side of the opinionated fence Chakrabati is seated.
Conclusions
In many a contentious debate it remains very difficult not to choose sides and to present information in a balanced fashion. Hopefully I have given free rein to both sides of the debate. This neutral stance was even more difficult given the extreme polarity involved in the two positions. I do hope readers will find this presentation interesting and will add to the current debate. As a personal matter I tend to side with those opposing big government and government intervention in general. As a matter of practical experience I have noted that whatever government can do, big business can do better, and often more efficiently. Much of the information and research conducted seems to also support this view.
As for net neutrality and its relationship with national security, I think that the information provided within the scope of this article helps to shed light on the question at hand. It appears clear that there is definitely a connection between the two phenomena; however, that relationship is contentious and problematic at best. The net neutrality crowd who cheered the arrival of net neutrality and government oversight may well rue the day they ever requested such intervention in the first place. Far from guaranteeing the free flow and ease of access desired, government oversight and bureaucracy risks having the reverse effect, if history is anything to go by. According to the Centre For Individual Freedom (CFIF), they also insightfully defined net neutrality six years ago: “’Net-Neutrality,’ or more aptly ‘Net Regulation,’ is governmental regulation of the internet.”[12] This offers a very clear and precise definition; “government regulation,” no more, no less. According to their view, the results of government regulation would be the same mediocre overly bureaucratised service for all. Indeed, such a democratic platform would ostensibly make all bytes equal, but by the same token, government owned, operated and controlled and mismanaged.
Notes
[1] See for instance: Kellon, L., 2012. US resists control of internet passing to UN agency. [Online] Accessed 27 March 2015]; Kiss, J., 2012. Who controls the Internet?. [Online] [Accessed 25 March 2015]; Mirani, L., 2014. When net neutrality backfires: Chile just killed free access to Wikipedia and Facebook. [Online] [Accessed 8 March 2015].
[2] Walker, L., 2014. How is Net Neutrality Working for the Countries That Have It?. [Online] [Accessed 24 March 2015].
[3] Ibid.
[4] Refer to: Walker, L., 2014. How is Net Neutrality Working for the Countries That Have It?. [Online] [Accessed 24 March 2015]; and BBC, 2014. Net Neutrality Law Adopted by European Parliament. [Online] [Accessed 24 March 2015].
[5] Refer to: Ruiz, R. R., 2015. F.C.C. sets Net Neutrality Rules. [Online] [Accessed 14 March 2015].
[6] See for instance: Phys.org, 2015. US lawsuit challenges legality of NSA online snooping. [Online]
[Accessed 12 March 2015].Press, T. A., 2014. Vodafone reveals scale of gov’t snooping in phone networks. [Online]
[Accessed 4 April 2015].Times, T. W., 2014. Lawmakers probing NSA face German secrecy hurdles. [Online][Accessed 5 April 2015].
[7] Stalla-Bourdillon, S., Papadaki, E. & Chown, T., 2014. From Porn to Cybersecurity Passin by Copyright: How mass surveillance tchnologies are gaining legitimacy…The case of deep packet inspection technologies. Computer Law and Security Review, 30(6), pp. 670-686.
[8] Ibid, pp, 671 – 674.
[9] BBC, 2014. Net Neustrality Law Adopted by European Parliament. [Online] [Accessed 24 March 2015].
[10] NetCompetition, 2009. Why New WH Cybersecurity Focus is a Game-Changer — for the Internet and Net. [Online] [Accessed 5 April 2015].
[11] Ibid
[12] CFIF, 2009. Net “Neutraliy”: Regulating and Politicizing the Internet. [Online] [Accessed 5 April 2015].
References
Ammori, M., 2014. The Case for Net Neutrality: What’s wrong with Obama’s internet policy. [Online] [Accessed 27 March 2015].
BBC, 2014. Net Neutrality Law Adopted by European Parliament. [Online] [Accessed 24 March 2015].
Becker, G. S., Carlton, D. W. & Sider, H. S., 2010. Net Neutrality and Consumer Welfare. Journal of Competition Law & Economics, 6(3), pp. 497-519.
Boliek, B., 2014. Politico: Tom Wheeler scrambles to salvage net neutrality plan. [Online] [Accessed 15 August 2014].
Carpenter, T. A., 2015. How Might Scholarly Communication Benefit from Net Neutrality?. [Online] [Accessed 12 March 2015].
CFIF, 2009. Net “Neutraliy”: Regulating and Politicizing the Internet. [Online] [Accessed 5 April 2015].
Chakrabati, S., 2006. Net Neutrality: Essential to national security. [Online] [Accessed 5 April 2015].
Cheng, A.-S.et al., 2012. The Role of Innovation and Wealth in the Net Neutrality Debate: A conant Analysis of Human Values in Congressional and FCC Hearings. Journal of the Association for Information Science and Technology, July, 63(7), pp. 1360-1373.
EDRi, 2013. Net Neutrality. The EDRi papers, 5 November, pp. 1-26.
Estes, A. C., 2015. Net Neutrality Wins: What Now?. [Online] [Accessed 8 March 2015].
FCC, 2015. Chairman Wheeler Proposes New Rules for Protecting the Open Internet. [Online] [Accessed 4 April 2015].
Geneva Internet Platform, 2015. Net Neutrality in Focus. [Online] [Accessed 24 March 2015].
Greenfield, R., 2006. The Net Neutrality Debate: The basics. The Educause Review, May/June, 41(3), pp. 82-83.
Kellon, L., 2012. US resists control of internet passing to UN agency. [Online] [Accessed 27 March 2015].
Kiss, J., 2012. Who controls the Internet?. [Online] [Accessed 25 March 2015].
Layton, R., 2014. Fact versus theory in the net neutrality debate. [Online] [Accessed 11 Marcch 2015].
Macri, G., 2015. FCC Confirms New Net Neutrality Rules Give Government Control Over Internet Rates. [Online]
[Accessed 20 March 2015].
McMillan, R., 2014. What Everyone Gets Wrong in the Debate Over Net Neutrality. [Online] [Accessed 24 March 2015].
Mirani, L., 2014. When net neutrality backfires: Chile just killed free access to Wikipedia and Facebook. [Online]
[Accessed 8 March 2015].
NetCompetition, 2009. Why New WH Cybersecurity Focus is a Game-Changer — for the Internet and Net. [Online]
[Accessed 5 April 2015].
Nunziato, D. C., 2008. Virtual Freedom: Net Neutrality, Free Speech, and Democracy in the Internet Age. 0 ed. Stanford: Stanford University Press.
Piper, P., 2010. Nets of Terror: Terrorist Activity on the Internet. In: T. J. Badey, ed. Violence anTerrorism 10/11. Boston: McGraw Hill, pp. 107-114.
Ruiz, R. R., 2015. F.C.C. sets Net Neutrality Rules. [Online] [Accessed 14 March 2015].
Rushe, D., 2015. Net neutrality activists score landmark victory in fight to govern the internet. [Online] [Accessed 8 March 2015].
Suderman, P., 2015. FCC Chairman Says Net Neutrality Won’t Mean New Internet Taxes. Here’s Why One Agency Commissioner Says That’s Wrong. [Online] [Accessed 16 March 2015].
United Nations News Center, 2015. UN expert applauds US decision guaranteeing ‘net neutrality’. [Online][Accessed 28 February 2015].
Walker, L., 2014. How is Net Neutrality Working for the Countries That Have It?. [Online] [Accessed 24 March 2015].
Further Reading on E-International Relations
- Opinion – Non-Military Threats and the Limits of National Security
- How Taiwan Tacitly Promotes its National Security Agenda
- Considering the Whole Ecosystem in Regulating Terrorist Content and Hate Online
- Provoking to Avoid War: North Korea’s Hybrid Security Strategies
- Opinion – Dangers Within Humanitarianism to Israel’s National Security
- Cyberspace and the Struggle to Maintain and Manage It